
Best practices in call center security include implementing strict password policies, using two-factor authentication for sensitive accounts, regularly backing up important data, securing physical access to the call center, and providing regular security training for employees. It's also important to monitor network traffic and keep security software up-to-date to prevent cyber attacks. Additionally, having a clear incident response plan in place can help ensure that the call center is prepared to handle security breaches or other emergencies.
Threat actors may sell customer data on the black market, where it can be bought and sold by other criminals. This can include forums, websites, and other online platforms that are specifically designed to facilitate the buying and selling of stolen data. These platforms may be hidden on the dark web and can be difficult to locate or access without the appropriate tools and knowledge. Additionally, threat actors may sell stolen data directly to other criminals, either through direct contact or through intermediaries. This can include data brokers, who buy and sell large quantities of stolen data, or specialized criminal organizations, such as identity theft or credit card fraud rings. By selling customer data on the black market, threat actors can generate significant profits, making this a lucrative activity for criminals.Implementing a strict password policy can improve call center security by making it more difficult for unauthorized individuals to gain access to sensitive accounts and systems. This can include requiring employees to use complex passwords that are difficult to guess or hack, setting expiration dates for passwords so that they must be changed regularly, and not allowing employees to reuse old passwords. By making it harder for unauthorized individuals to gain access to accounts, a strict password policy can help prevent data breaches and other security incidents. Additionally, by regularly updating and changing passwords, a strict password policy can help to prevent long-term unauthorized access to accounts.
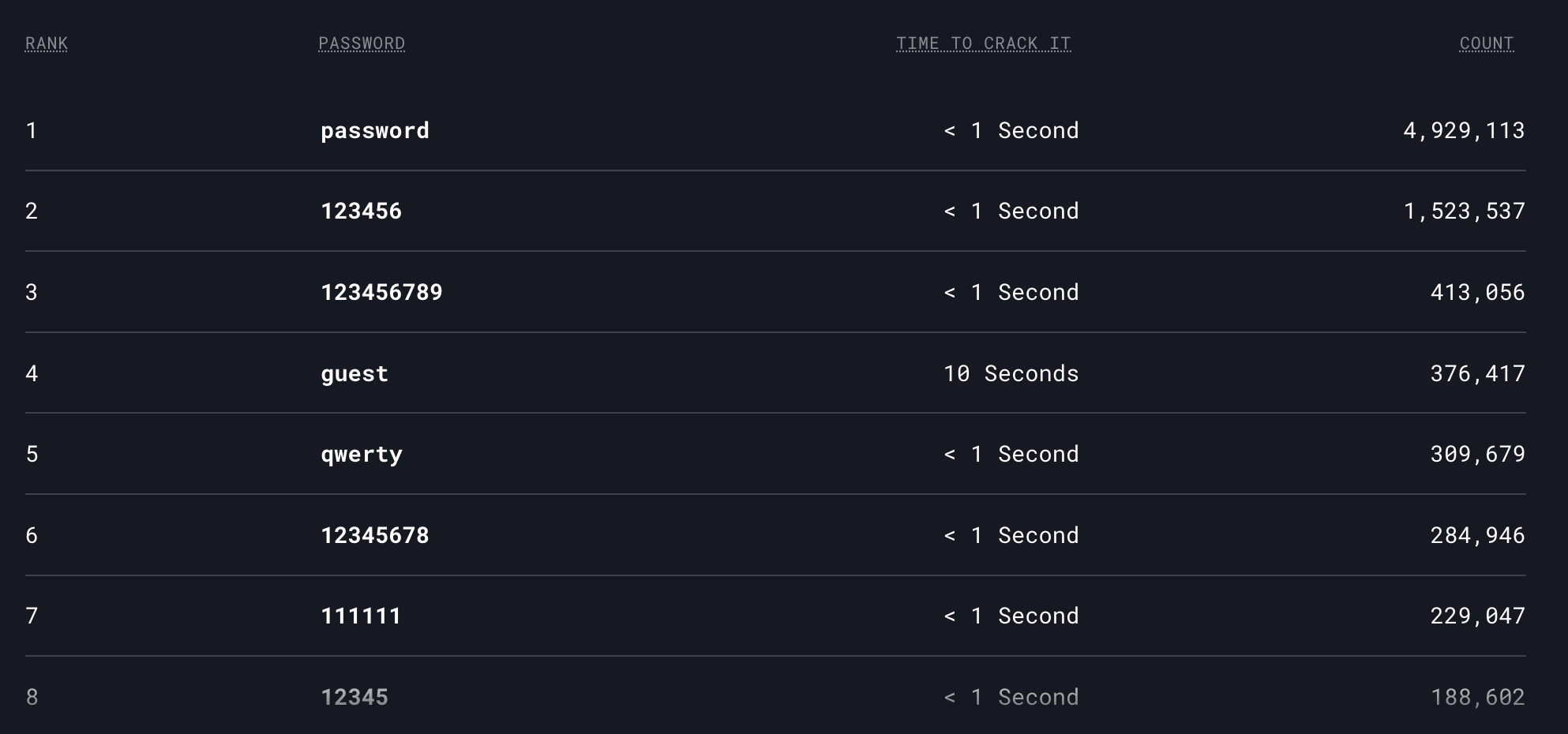
Source: NordPass 2022 Most Common Passwords
In addition to creating policies that require a combination of letters, numbers and characters, companies are advised to manage a disallow list that contains the most common passwords.
The same goes for phone PINs. These are usually 4 digit codes that customers create to access their account or prove their identity over the phone or other device (ATM). PINs should be 6 digits or more in length, and disallow the most common codes (e.g. 1234), and especially pins that start with 19 or 20 for birth years.
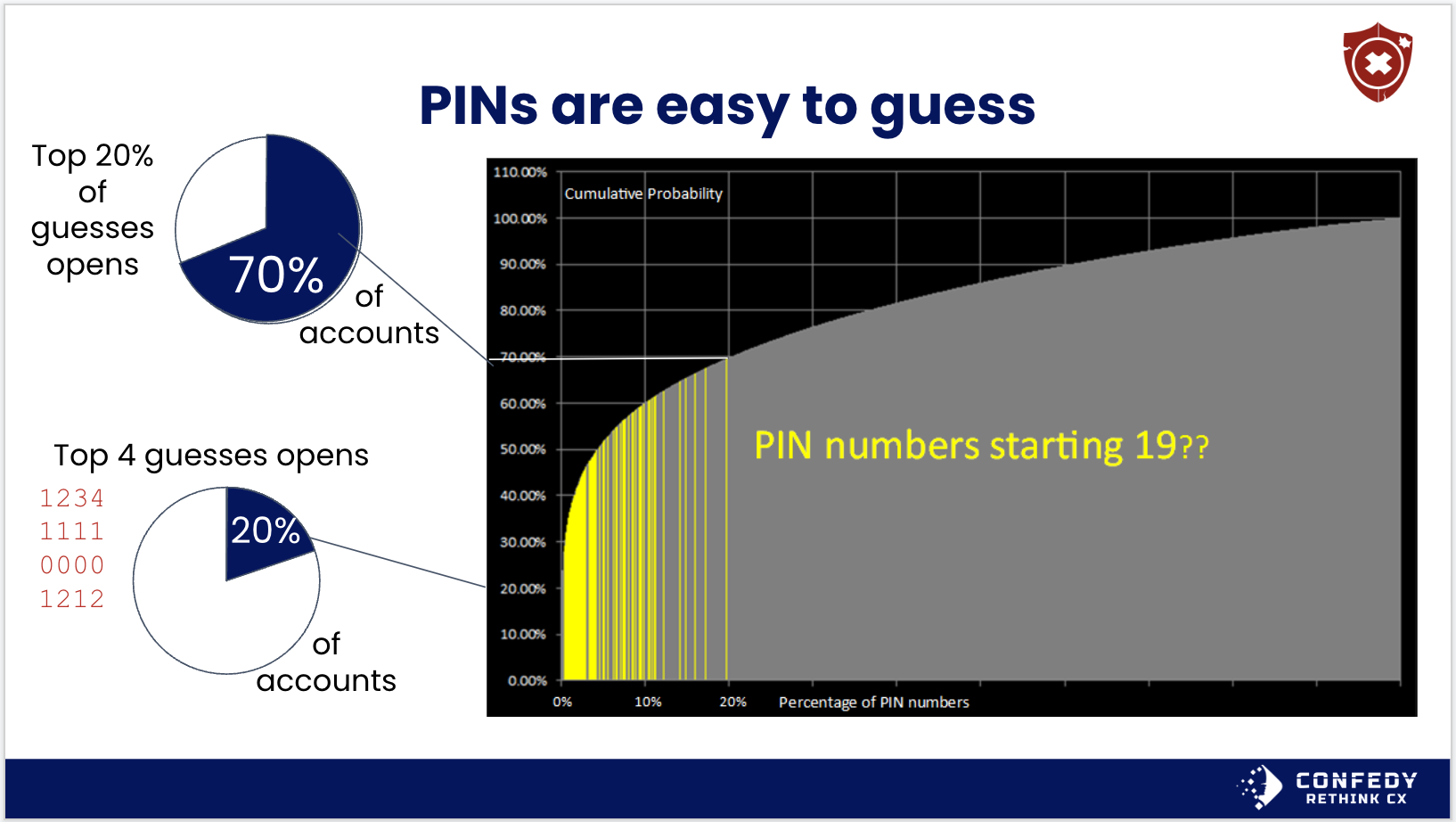
Source: Based on data from DataGenetics
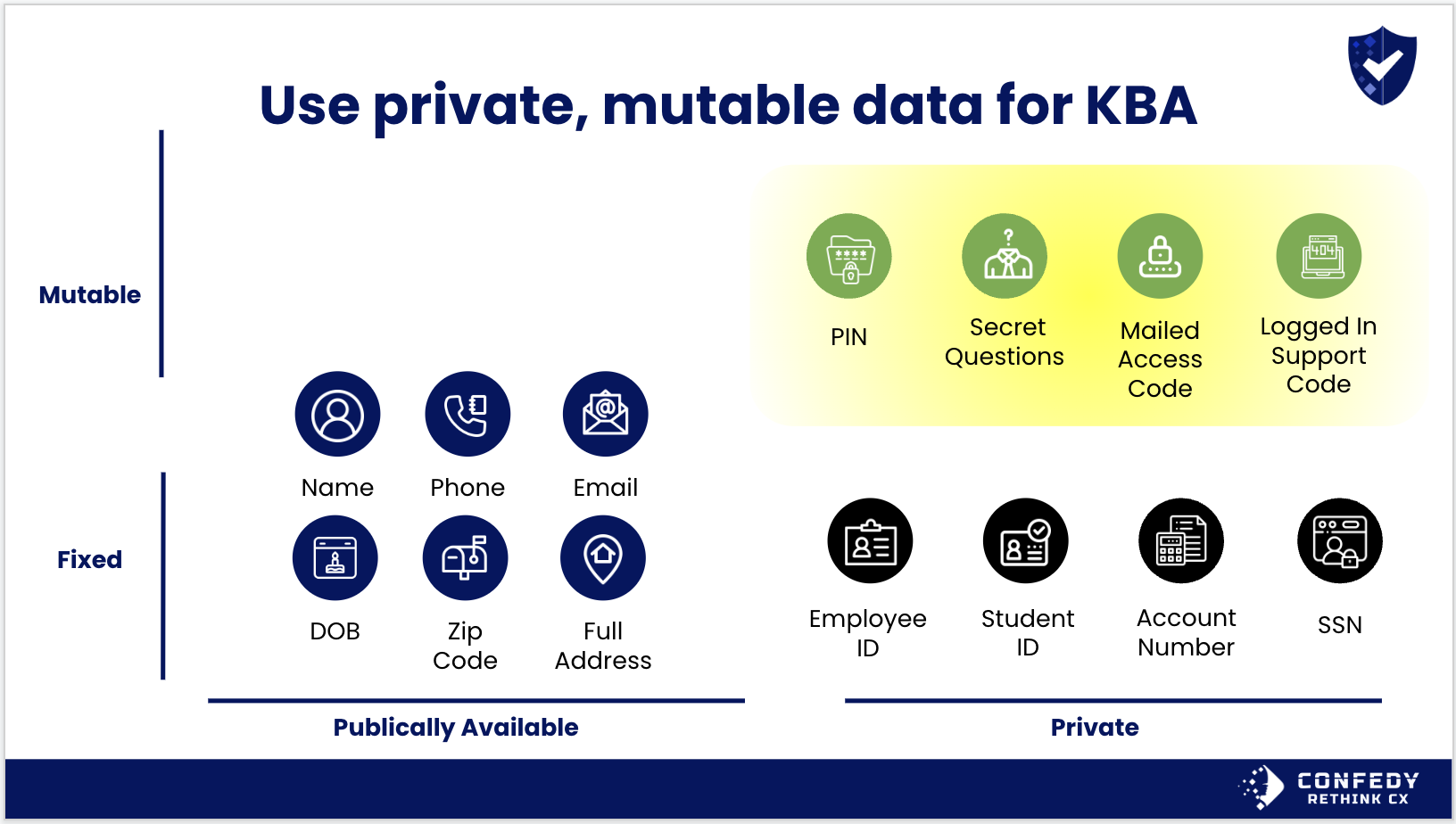
If you are going to rely on KBA, the best practice is to require datapoints that are private and mutable as shown in the table below. This includes long and secure PINs, unique secret questions, physically mailed access codes or support codes the customer can only get once they are logged into their online account.
Two-factor authentication, also known as 2FA, is a security measure that requires users to provide two different authentication factors in order to access an account. This can include something the user knows (such as a password), something the user has (such as a security token or a mobile phone), or something the user is (such as a fingerprint or facial recognition data). By requiring two different factors for authentication, 2FA makes it much more difficult for unauthorized individuals to gain access to sensitive accounts. This can help to prevent identity fraud, because even if an attacker is able to obtain a user's password, they will still be unable to access the account without the second authentication factor. Additionally, 2FA can help to prevent unauthorized access if a user's password is stolen or otherwise compromised. Multi-factor allows customers to have more than one additional factor such as SMS plus authenticator app plus recovery codes, using the strongest first.
There are several steps that companies can take to secure physical access to the call center, including:
By taking these steps, companies can help to prevent unauthorized access to the call center and protect against potential security threats. It's important to regularly review and update security measures to ensure that they remain effective.
Regular security training for inbound agent training can include topics such as password security, phishing scams, compliance requirements, security metrics and how to recognize and report security threats in real-time. It can also include training on the company's specific security best practices, and special policies and procedures, such as how to handle sensitive data and what to do in the event of a security breach. This type of training can help to ensure that call center agents are aware of potential security risks and know how to protect the company's sensitive information. Training is most critical for inbound call agents, and anyone in healthcare and banking. Outbound sales and telemarketing calls are less frequently subject to active fraud attempts but all agents should be included in training. Regular security training can also help to reinforce the importance of security and remind employees of the role they play in protecting the company's assets.
Limiting call agent privileges can be an important part of a cybersecurity protection strategy for contact centers. By limiting the privileges of call agents, contact centers can reduce the risk of unauthorized access to sensitive information or systems. This can include restricting access to specific network resources, such as servers or databases, or limiting the ability of call agents to install or execute certain types of software. By limiting privileges in this way, contact centers can help to prevent attacks or accidents that could compromise sensitive information or disrupt operations. Additionally, limiting call agent privileges can help to ensure that call agents are only able to access the information and resources that they need to perform their job duties, and can help to prevent unnecessary or unauthorized access to sensitive data. Overall, limiting call agent privileges can be an effective way to improve cybersecurity protection in contact centers.
Enforcing the use of password managers for call agents can be an effective way to improve security in contact centers. Password managers are software tools that are designed to help users securely store and manage their passwords. They can generate strong, unique passwords for each account that a user has, and can store these passwords in an encrypted format. This can help to prevent password reuse, which is a common issue that can lead to security breaches. By enforcing the use of password managers, contact centers can help to ensure that call agents are using strong, unique passwords for their accounts, and can reduce the risk of password-related security incidents. Additionally, password managers can help to simplify the process of managing multiple passwords, which can improve the efficiency and productivity of call agents. Overall, enforcing the use of password managers can be an effective way to improve security and protect against password-related threats in contact centers.
White-hat hackers, also known as ethical hackers, are individuals who use their hacking skills to help organizations identify and address security vulnerabilities. They can help companies protect against infiltration attempts at social engineering by simulating these types of attacks and testing the organization's defenses. This can include sending phishing emails or other messages to employees, attempting to gain unauthorized access to systems or networks, or using other tactics that are commonly used by attackers. By simulating these attacks, white-hat hackers can help companies to identify weaknesses in their security systems and take steps to address them. This can include implementing stronger authentication controls, providing training to employees on how to recognize and report social engineering attempts, or implementing other security measures. Overall, white-hat hackers can play a valuable role in helping companies protect against infiltration attempts at social engineering.
Call recordings can help call centers with their security by providing a record of interactions between call agents and customers. This can be useful for several reasons. For example, call recordings can be used to monitor and evaluate the performance of call agents, to ensure that they are providing accurate and consistent information to customers. Call recordings can also be used to detect and investigate potential security incidents, such as attempts to gain unauthorized access to customer accounts or to steal sensitive information. Additionally, call recordings can be used as evidence in the event of a security breach or other incident, to support any investigations or legal proceedings. Overall, call recordings can provide valuable information and support for call centers, and can help to improve their security posture.
VOIP, or Voice over Internet Protocol, can be an important consideration for call center security. VOIP is a technology that allows voice communications to be transmitted over the internet, rather than over traditional phone lines. This can provide several benefits for call centers, including lower costs, greater flexibility, and the ability to handle large volumes of calls. However, VOIP can also introduce new security challenges, as it relies on the internet to transmit voice data. This can make it more vulnerable to attacks, such as eavesdropping or denial of service attacks, which can disrupt call center operations and compromise sensitive information. As a result, it is important for call centers that use VOIP to implement appropriate security measures, such as encryption, access controls, and network monitoring, to protect against these types of threats.
Anti-virus software can help customer care centers to stay protected against identity threats. Anti-virus software is a type of security software that is designed to detect and remove malicious software, such as viruses, worms, and Trojan horses. It works by scanning the contact center's systems and networks for known threats, and can either remove the threats automatically or alert the administrator so that they can take appropriate action. By using anti-virus software, contact centers can help to prevent malware infections and other security incidents that could compromise sensitive information or disrupt operations. Additionally, anti-virus software can help to reduce the risk of data breaches, which can have serious consequences for contact centers and their customers. As a result, using anti-virus software can be an important part of a comprehensive security strategy for customer care centers.
When companies monitor network traffic, they are looking for unusual or suspicious activity that may indicate a security threat. This can include scanning for malware or other malicious software, tracking network usage to identify potential security breaches, and monitoring network traffic for signs of unauthorized access or data leakage. By monitoring network traffic, companies can identify potential security threats and take action to prevent or mitigate them. This can help to protect the company's sensitive information and prevent data breaches or other security incidents. Additionally, by monitoring network traffic, companies can identify and resolve network performance issues, such as congestion or bottlenecks, which can help to improve overall network reliability and performance.
There are several steps that companies can take to keep their security software up-to-date, including: 1. Configuring the software to check for and automatically install updates. 2. Regularly reviewing and updating security software to ensure that it is the latest version. 3. Setting up alerts or notifications to remind staff to check for and install updates. 4. Keeping an inventory of security software and its versions, to ensure that all systems are up-to-date. 5. Monitoring the software vendor's website or other sources for information on updates and security patches. By taking these steps, companies can help to ensure that their security software is always up-to-date and able to provide the latest protections against security threats. It's important to regularly review and update security software to ensure that it remains effective and can protect against new and emerging threats.
Firewalls play an important role in contact center security by helping to protect against unauthorized access to the contact center's networks and systems. A firewall is a network security system that is designed to control incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between the contact center's networks and the internet, and can prevent unauthorized access to the contact center's systems by blocking potentially dangerous or malicious traffic. Firewalls can be implemented as hardware or software, and can be configured to allow or block specific types of traffic, such as incoming connections from specific IP addresses or outgoing traffic to certain websites. By using firewalls, contact centers can help to prevent attacks and protect against data breaches and other security threats.
Call center compliance refers to the process of ensuring that a call center is compliant with relevant laws, regulations, and industry standards. This can include complying with laws that relate to consumer protection, data privacy, and other areas that are relevant to the call center's operations. Compliance can also include meeting the requirements of industry standards, such as the Payment Card Industry Data Security Standard (PCI DSS) for call centers that handle payment card data. By ensuring compliance with relevant laws and standards, call centers can help to protect their customers and avoid fines, penalties, and other negative consequences that may result from non-compliance. Compliance is an ongoing process, and call centers must regularly review and update their policies and procedures to ensure that they are meeting the relevant requirements.
PCI DSS stands for Payment Card Industry Data Security Standard. It is a set of security standards that are designed to protect the confidentiality and integrity of payment card data. The PCI DSS is developed and maintained by the Payment Card Industry Security Standards Council (PCI SSC), which is a consortium of payment card companies, including Visa, Mastercard, American Express, and Discover. The PCI DSS includes requirements for maintaining a secure network, protecting cardholder data, implementing strong access controls, regularly monitoring and testing networks, and maintaining an information security policy. It is a widely-adopted standard that is used by businesses and organizations around the world to ensure the security of payment card data.
PCI compliance is important for contact centers, especially if they handle payment card data. The PCI DSS is a set of security standards that are designed to protect payment card data, and compliance with these standards is a requirement for businesses and organizations that handle this type of information. By achieving PCI compliance, contact centers can demonstrate that they have implemented appropriate security controls to protect payment card data, which can help to build trust with customers and prevent data breaches or other security incidents. Additionally, PCI compliance can help to ensure that contact centers are meeting legal and regulatory requirements, and can help to prevent financial losses due to fines or other penalties.
Contact centers that handle payment card data must take steps to protect credit card numbers and other sensitive information from unauthorized access or disclosure. There are several measures that contact centers can take to protect credit card numbers, including:
An effective cybersecurity incident response plan should include several key elements, such as:
There are several certifications that contact centers can earn to demonstrate that they are adequately protected against would-be hackers. These certifications are typically awarded by industry organizations or regulatory bodies, and can provide a valuable indication of the contact center's security practices and capabilities. Some examples of certifications that contact centers can earn include:
While not strictly concerned with identity fraud, a related topic is privacy and the regulations around it. Contact centers that operate in the European Union (EU) or handle the personal data of EU citizens are required to comply with the General Data Protection Regulation (GDPR). This is a law that was introduced in 2018 to regulate the collection, use, and storage of personal data. It applies to any organization that processes the personal data of EU citizens, regardless of where the organization is located. The GDPR sets out strict rules for the handling of personal data, and requires organizations to have appropriate security measures in place to protect this data from unauthorized access or disclosure. Additionally, the GDPR gives individuals the right to access, rectify, erase, or restrict the processing of their personal data. As a result, contact centers that operate in the EU or handle the personal data of EU citizens must be familiar with the requirements of the GDPR and take appropriate steps to comply with the law.
CCPA stands for the California Consumer Privacy Act, which is a law that was enacted in 2018 to regulate the collection, use, and sharing of personal information of California residents. The CCPA applies to businesses and organizations that collect the personal information of California residents, and it gives individuals the right to access, delete, or opt-out of the sale of their personal information. The CCPA also imposes strict requirements on businesses and organizations that handle personal information, including the need to implement appropriate security measures to protect this information from unauthorized access or disclosure. As a result, contact centers that operate in California or handle the personal information of California residents must be familiar with the requirements of the CCPA and take appropriate steps to comply with the law.
HIPAA, or the Health Insurance Portability and Accountability Act, is a law that sets out requirements for the protection of personal health information. Contact centers that handle personal health information, such as medical records or insurance information, are required to comply with HIPAA. The HIPAA requirements that a contact center must follow include:
By complying with these requirements, contact centers can help to protect the personal health information of their customers and ensure that they are meeting their obligations under HIPAA.
Companies that do not have adequate call center security controls in place are at risk of experiencing a range of negative consequences. This can include data breaches and other security incidents, which can result in the loss or theft of sensitive information. This can damage the company's reputation and lead to financial losses, such as the cost of responding to the incident and any legal or regulatory penalties. In some cases, security incidents can also result in downtime or other disruptions to the company's operations, which can have a negative impact on productivity and customer satisfaction. Additionally, companies that do not have adequate security controls in place may be at a competitive disadvantage, as customers and clients may be more likely to choose businesses that have a proven track record of protecting their sensitive information.
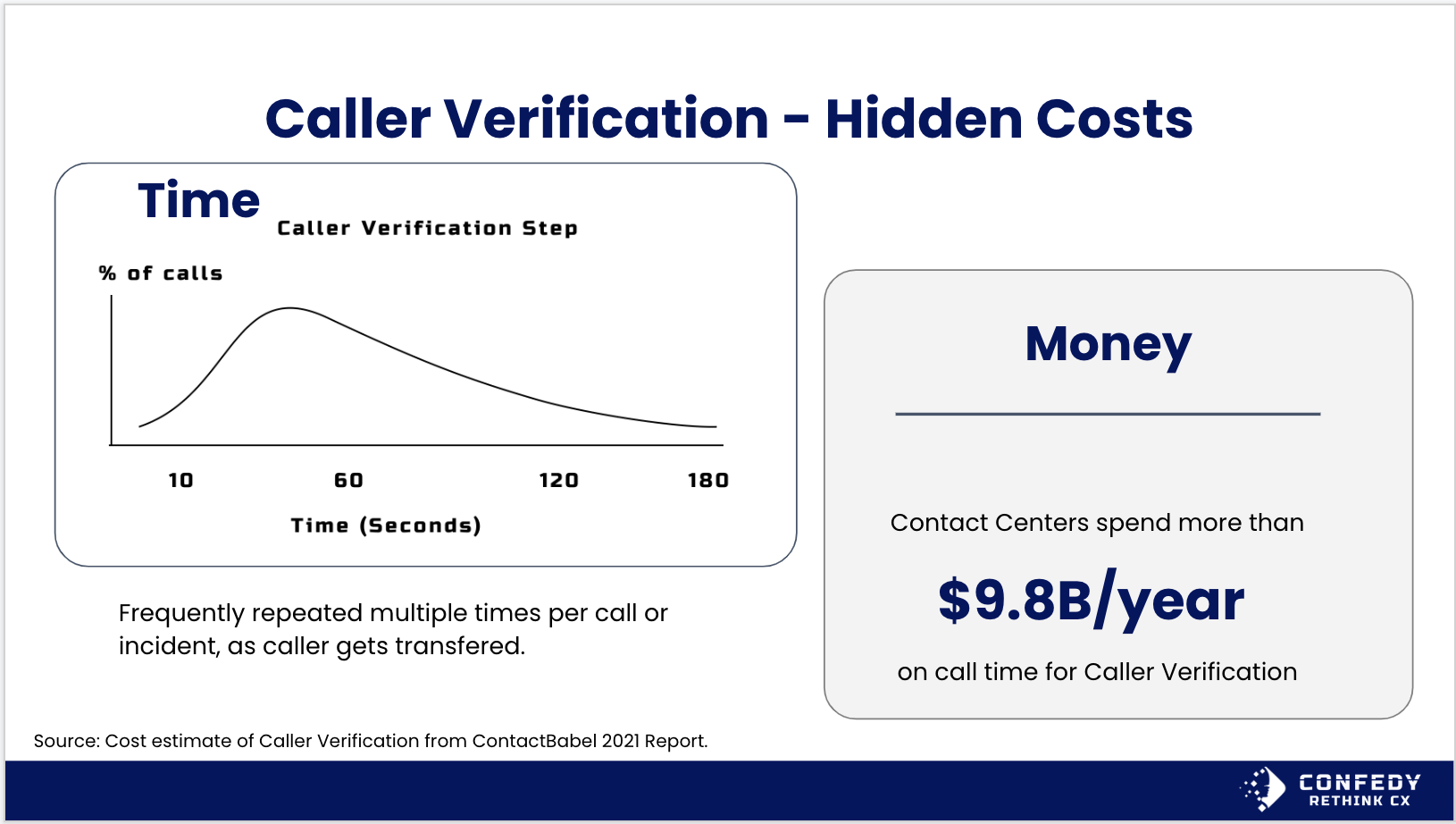
Some of the costs are straightforward to calculate. The time it takes for agents to conduct a caller verification process is significant. It can take a minute or more per call, and that adds up to $9.8B spent across the call center and customer service industry, according to Contact Babel. Other costs, such as the impact to brand reputation, customer trust and stock price are harder to calculate but no less real.
Contact centers are often targeted by identity threat actors, who seek to gain unauthorized access to sensitive information or accounts. These threat actors can use a variety of tactics to try to breach a call center's security, such as phishing scams, social engineering, and malware attacks. Because contact centers often handle large amounts of sensitive information, such as customer account data and personal information, they can be attractive targets for identity threat actors. It's important for companies to implement strong security controls and regularly monitor for potential threats to protect against these types of attacks.
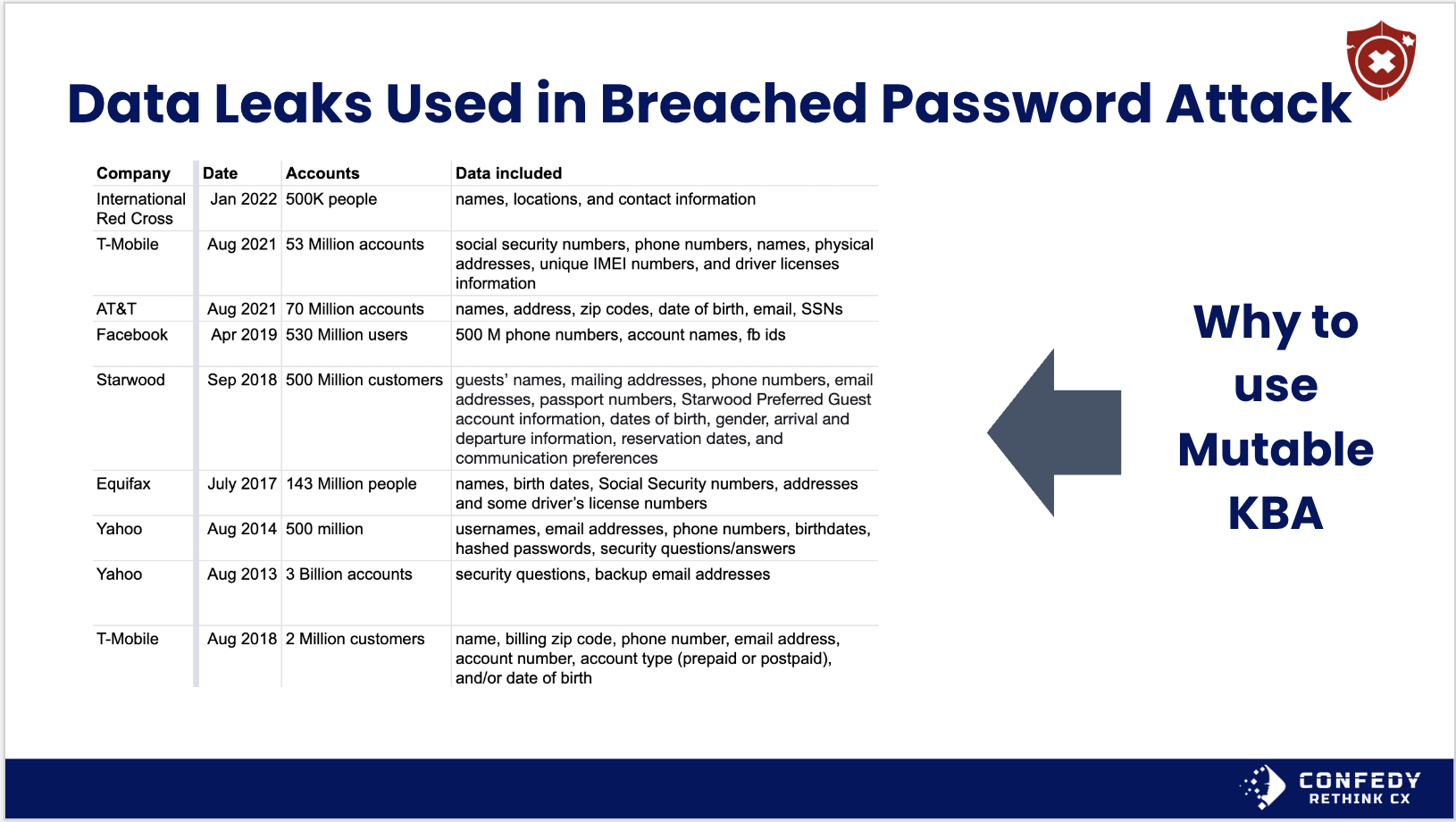
Table: Breached Password based attacks rely on information stolen in prior hacks.
Phishing scams are a type of cyber attack in which the attacker attempts to trick the victim into revealing sensitive information or taking a specific action, such as clicking on a malicious link. This is often done by sending the victim a fraudulent email or other message that appears to be from a legitimate source, such as a bank or a government agency. Some examples of phishing scams include:
Social engineering is often successful at fooling call agents because it relies on psychological manipulation rather than technical tricks or exploits. By using tactics such as building trust and rapport, appealing to the victim's emotions, or using seemingly legitimate information, attackers can often convince call agents to reveal sensitive information or take a specific action. This is particularly effective in a call center environment, where agents may be under pressure to handle a high volume of calls and may not have the time or resources to carefully verify the legitimacy of every request. Additionally, attackers may use personal information about the victim or the company to make their scams seem more convincing, which can further increase the likelihood of success.
Malware attacks can be used against contact centers in a variety of ways. For example, attackers may use malware to gain unauthorized access to the contact center's systems or networks, allowing them to steal sensitive information or disrupt operations. In some cases, attackers may use malware to create "back doors" that allow them to maintain ongoing access to the system, even after initial security measures have been put in place. Additionally, attackers may use malware to target individual employees, such as call center agents, in order to gain access to their accounts or systems. By using malware, attackers can often gain access to a contact center's systems without being detected, making it an effective tactic for breaching security.
Security measures can impact customer interactions when calling into a service provider for support in a variety of ways. For example, if the security measures are too strict or difficult to navigate, it can make it harder for customers to access the support they need. This can lead to frustration, long wait times, and a poor overall experience for the customer. On the other hand, if security measures are not strict enough, it can put sensitive customer information at risk and potentially lead to data breaches or other security incidents. This can also have a negative impact on customer experience, as customers may lose trust in the company and be less likely to use its services in the future. After routing the caller to a new department it's best to carry over the caller verification information, but this isn't always technically feasible. It's important for businesses to strike a balance between security and customer experience, and to regularly review and update their security measures to ensure that they are effective and do not negatively impact the customer experience.
KBA, or Knowledge-Based Authentication, is an older security measure that is used with the intent to verify the identity of a caller. This can include asking the caller to provide specific information, such as their date of birth or the last four digits of their social security number, to confirm that they are who they claim to be.
KBA may be going away in the future because it fails to adequately protect user accounts, while at the same time impacting customer experience negatively. While KBA can theoretically help to improve security by making it more difficult for attackers to impersonate legitimate users, the reality is that most - if not all - of the typical information asked for during KBA is publically available or easily discovered.
It can also impact the caller experience. For example, if the caller is not aware that they will be asked to provide specific information, they may become frustrated. Repeating PII to agents on the phone, and having to spell everything out, can be frustrating and time-consuming. Additionally, if the caller is unable to provide the requested information, they may be unable to access the support they need. As a result, KBA can have a negative impact on caller experience if it is not implemented carefully and effectively.
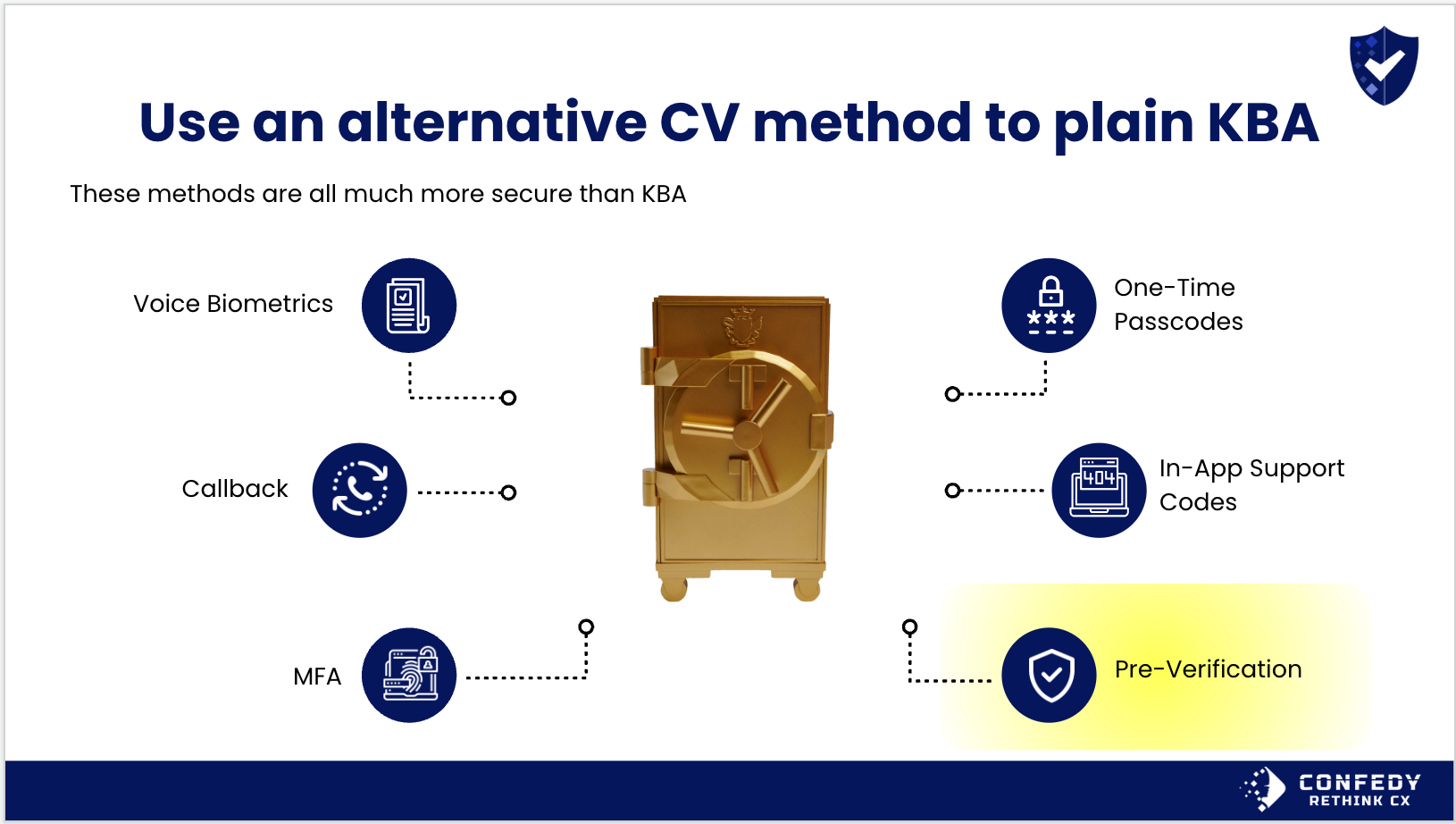
Caller Verification (CV) is the lynchpin of identity security for customer support and customer service operations. There are newer options for how to perform this step.
Automatic Number Identification (ANI), or more commonly referred to as Caller Id, is vulnerable to spoofing and therefore should not be trusted. There are industry initiatives designed to help, such as Shaken-Stir, but the adoption has slowed and then reversed.
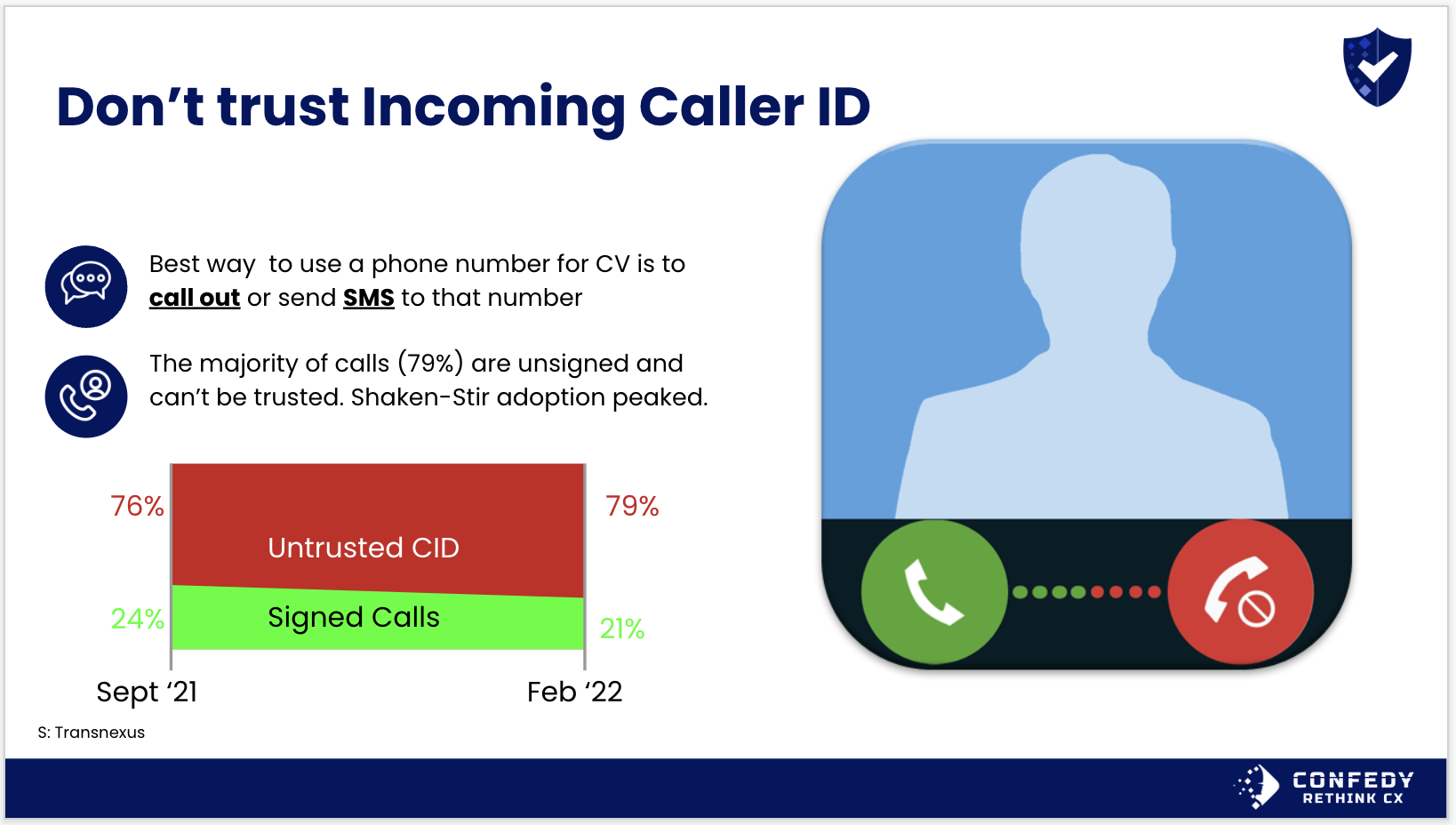
Fraudsters utilize free automation software on their laptop to dial into service providers spoofing the number of the customer they are pretending to be. This is used for B2C hacks as well as infiltrating B2B environments where they will spoof an internal phone number, dial into the technical support department, and hope to gain access to internal systems with high-level privileges.
Voice recognition, also known as voice biometrics, can be used to verify a caller's identity. Voice recognition technology uses algorithms to analyze the unique characteristics of an individual's voice, such as pitch, tone, and cadence. By comparing the caller's voice to a pre-recorded sample, voice recognition technology can determine the caller's identity with a high degree of accuracy. This can be used to verify the caller's identity before allowing access to sensitive information or services. Voice recognition can provide a convenient and secure way to verify a caller's identity, and can be an effective alternative to other authentication methods, such as passwords or security questions. Additionally, voice recognition can be useful for contact centers that handle a large volume of calls, as it can automate the authentication process and reduce the need for manual intervention.
There are some downsides to voice biometrics, starting with the reality that many consumers are uncomfortable from a privacy perspective having their voices recorded and fingerprinted. Therefore many people do not agree to opt-in. Also, it must be paired with another verification method initially, so it is not a primary method of verifying a caller. However, it can save time in subsequent calls. On the other hand, systems that rely on voice biometrics sometimes need to ask a few questions to get enough sample data to match against. So this minimizes the time savings.
Phone printing is a type of call center software that is used to identify and verify the identity of a caller based on the unique characteristics of their phone. This can include factors such as the phone's hardware, software, and network information. By analyzing these characteristics, phone printing technology can create a unique "fingerprint" for the phone, which can be used to identify and verify the caller's identity. This can provide a convenient and secure way to authenticate the caller's identity, and can be an effective alternative to other authentication methods, such as passwords or security questions. Additionally, phone printing technology can be useful for contact centers that handle a large volume of calls, as it can automate the authentication process and reduce the need for manual intervention. Overall, phone printing technology can be an effective tool for improving security and protecting against identity fraud in contact centers.
Caller pre-verification is a process that is used to verify the identity of a caller before allowing them access to sensitive information or services. This can include using multi-factor authentication methods, such as an SMS or authenticator app before connecting them with an agent. By pre-verifying the caller's identity, contact centers can help to prevent social engineering and protect against identity fraud. Additionally, caller pre-verification can help to improve the efficiency of the call center, by reducing the need for manual intervention and allowing call agents to focus on providing support and assistance to verified callers. Overall, caller pre-verification can be an important part of a comprehensive security strategy for contact centers.
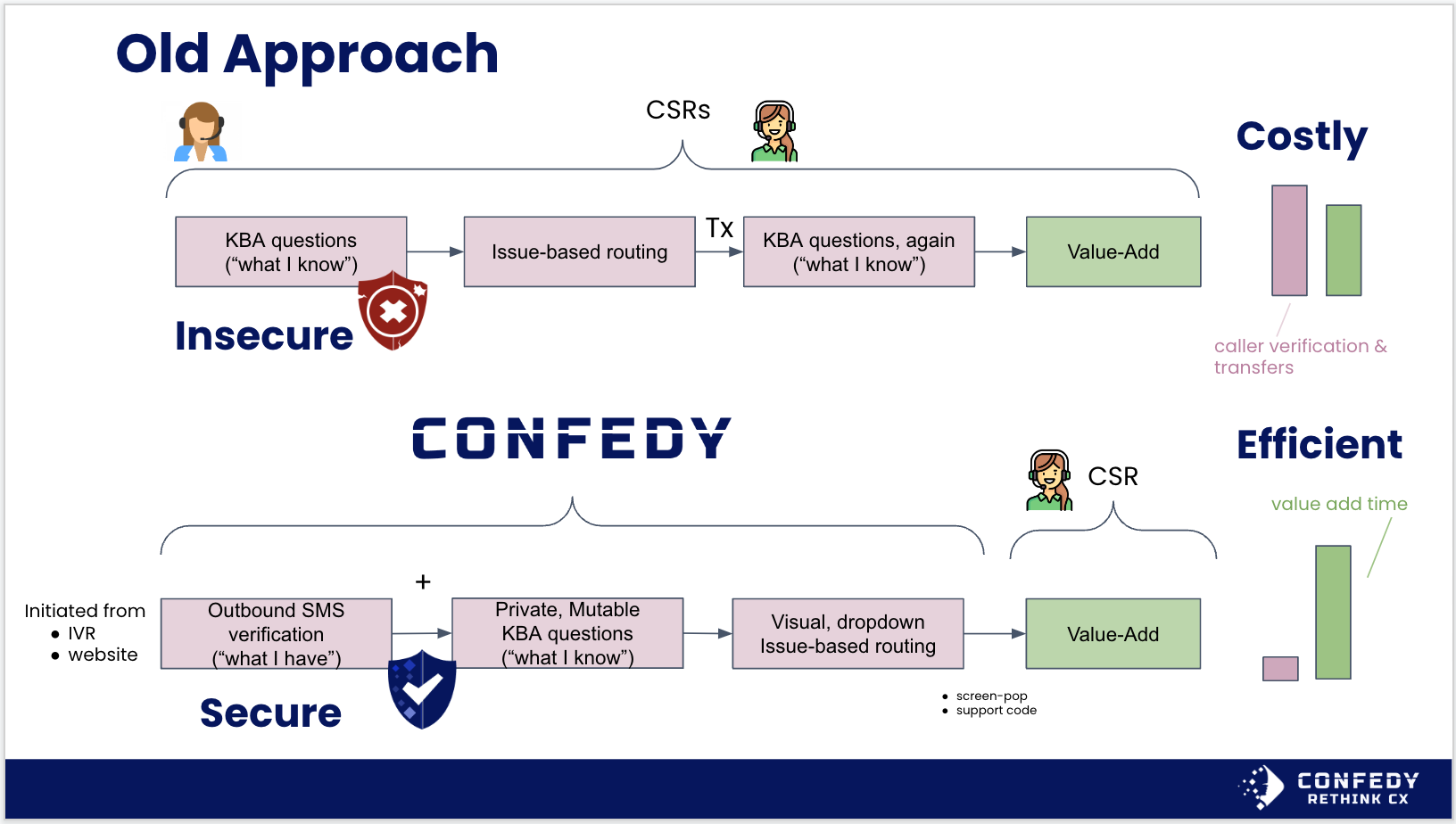
Confedy's pre-verification technology can use a variety of techniques to confirm the caller owns the mobile phone number and/or email (“what I have”). Plus, it can handle the private, mutable KBA exchange (“what I know”) - all before talking to an agent. Importantly, these pre-verification methods are not vulnerable to number spoofing. Taking verification out of the agent's hands also removes social engineering as an attack vector. Security is greatly enhanced while also saving time for callers & agents.
It is generally believed that identity fraud is a growing problem, due in part to the increasing amount of sensitive information that is available online and the increasing sophistication of criminal groups who specialize in identity theft and other forms of fraud. Additionally, the rapid adoption of new technologies, such as online banking and mobile payment systems, has created new opportunities for identity fraud. As a result, it is likely that the prevalence of identity fraud will continue to increase in the future, unless appropriate measures are taken to prevent and detect this type of crime.
It is difficult to predict exactly what may change in the identity fraud landscape in the future, as there are many factors that can affect the prevalence and methods of this type of crime. However, some potential changes that may occur in the future include:
These are just a few examples of potential changes that may occur in the identity fraud landscape in the future. It is important for businesses and individuals to stay informed and take appropriate measures to protect themselves against this type of crime.
Confedy delivers a cloud-based Caller Verification solution that minimizes the attack surface for would-be threat actors. The platform utilizes multi-factor authentication and end-to-end encryption and sits on top of existing CCaaS software. It is designed for B2C organizations that have a high-volume inbound contact centers and high call transfer rate and need to balance strong identity security with enhanced customer experience.
Learn more at www.confedy.com
Keep on learning...
